Teaching
Advanced Computer Security
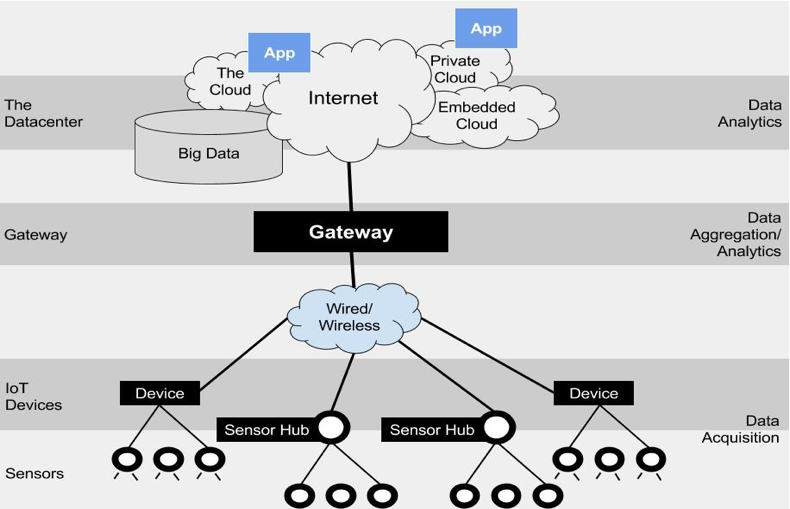
Tthe advanced security class focuses on autonomous security. As technology continues to advance rapidly, cyber threats are also becoming more sophisticated. Unfortunately, security protections cannot be handled alone by human analysts anymore, and we need more automated mechanisms to identify and respond to attacks. Artificial Intelligence (AI) is starting to play a critical role in cybersecurity by augmenting human analysts with automated threat detection and response capabilities. These agents, also known as AI-powered security solutions, use machine learning algorithms and other AI techniques to analyze vast amounts of data in real-time, identify abnormal behavior, and alert security teams to potential threats.
Cyber-Physical Systems Security and Privacy
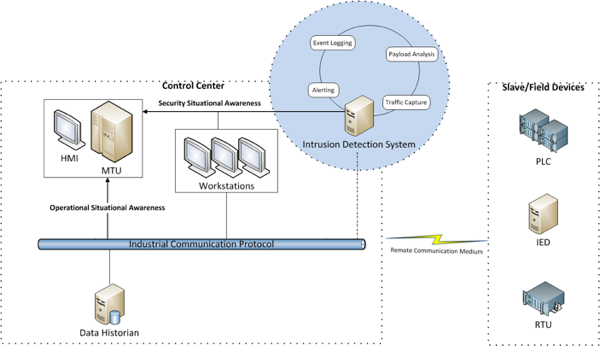
The Stuxnet attack was a wake-up call to improve the security of our critical infrastructures, which include transportation networks, the power grid, and other cyber-physical systems, where computation, communications, and control are tightly integrated. This class covers the security of cyber-physical systems from a multi-disciplinary point of view, from computer science security research (network security and software security), to public-policy (e.g., the Executive Order 13636), risk-assessment, business drivers, and control-theoretic methods to reduce the cyber-risk to cyber-physical critical infrastructures. We also discuss privacy issues related to the collection of human activity in cyber-physical systems.
Computer Security
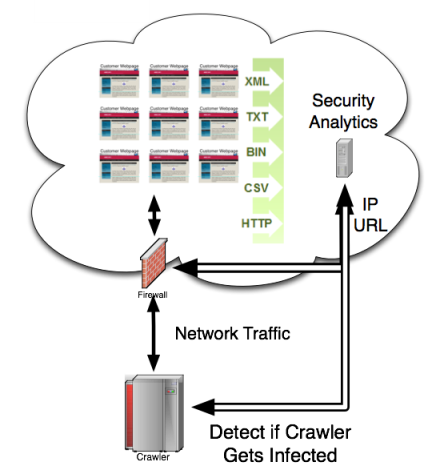
Information Security is a comprehensive study of the principles and practices of computer system security including operating system security, network security, software security, and web security. Topics include common attacking techniques such as memory exploits and command injection; applied cryptography, and key management; intrusion detection, and network monitoring; trusted computing; access control and security policies; password protection; and legal and ethical issues in computer security.

Security BootCamps K-12
TBD. Introduction to security and cryptography for K-12.
Resources
Web Quest Challenge
Discrete Math.
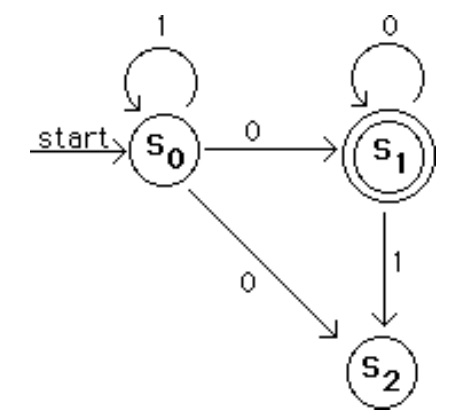
Discrete math introduces students to fundamental mathematical reasoning (axiomatic propositional and predicate logic, soundness and completeness), relations, search problems in graphs, automata theory, formal grammars, and Turing machines. We complement the regular textbook with the comic book: "Logicomix, An epic search for truth" by Apostolos Doxiadis and Christos Papadimitriou. Bloomsbury Publishing and Bloomsbury USA, September 2009.

Privacy in the Age of the Internet of Things
Course Website
In the 21st century computers have a variety of sensors that can collect more information about the world around them than what humans can type on keyboards. This ability of IoT devices to passively sense surrounding activity makes the privacy issues they raise distinct from the privacy issues raised by traditional computing systems. As they collect physical data of diverse human activities such as electricity consumption, location information, driving habits, and biosensor data at unprecedented levels of granularity, their passive manner of collection leaves people generally unaware of how much information about them is being gathered. One of the first priorities in addressing this problem is preparing a new generation of students versed in the multidisciplinary nature of privacy risks in the age of IoT. This multi-disciplinary course was developed in conjunction with Dr. Olivia Banner from the Emerging Media and Communication (EMAC) program and with support from Intel corporation. Throughout the course, EMAC majors pair with CS majors to help both groups think critically about new ways to improve our privacy protections in IoT.