CPS Security and Privacy
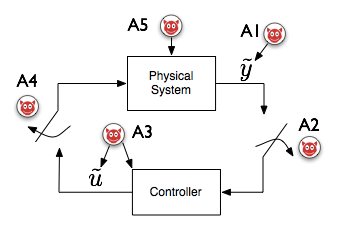
When we started working on Cyber-Physical Systems (CPS) Security in 2007, the field was very different to what it is now: the urgency for protecting control systems was not a priority in a pre-Stuxnet world. Several security researchers argued that there was nothing new about SCADA security because we only needed to apply best IT security practices to this field. Control theory researchers argued that injecting faults into systems was an old problem. We decided to brainstorm what was new and fundamentally different about CPS security when compared to IT security and to control theory, and published two workshop papers in 2008. The first one identifying how CPS security was different from previous work in control theory, and the second paper on how CPS security was different from traditional IT security best practices (and why the problem was important):
Secure Control: Towards Survivable Cyber-Physical Systems First International Workshop on Cyber-Physical Systems, 2008.
Research Challenges for the Security of Control Systems. 3rd Workshop on Hot Topics in Security (HotSec), 2008.
A more recent manuscript created for the Cyber-Security Body of Knowledge (CyBok) summarizes the field of CPS Security:
Cyber-Physical Systems Security Knowledge Area. The Cyber Security Body of Knowledge. 2019.
Detecting Attacks in Cyber-Physical Systems
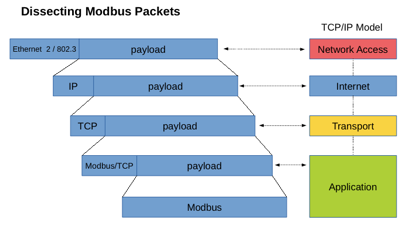
One of our main lines of work is to use physics-based anomaly detection in CPS. We have developed parsers for a variety of industrial control protocols to do deep-packet inspection and capture the physical evoluation of the state of the system in order to identify anomalies and potential false-data injection attacks. We are also looking into novel ways to detect attacks in other cyber-physical systems, like our proposal on visual challenges to verify the integrity of remote surveillance cameras.
SAVIOR: Securing Autonomous Vehicles with Robust Physical Invariants USENIX Security 2020.
Adversarial Classification under Differential Privacy NDSS 2020.
Limiting the Impact of Stealthy Attacks on Industrial Control Systems 23rd ACM Conference on Computer and Communications Security (CCS) 2016.
A Survey of Physics-Based Attack Detection in Cyber-Physical Systems> ACM Computing Surveys. 2018.
Attacks Against Process Control Systems: Risk Assessment, Detection, and Response ACM Symposium on InformAtion, Computer, and Communications Security (ASIACCS) 2011.
Evaluating Electricity Theft Detectors in Smart Grid Networks Research in Attacks Intrusions and Defenses Symposium (RAID) 2012.
Using Visual Challenges to Verify the Integrity of Security Cameras 31st Annual Computer Security Applications Conference (ACSAC) 2015.
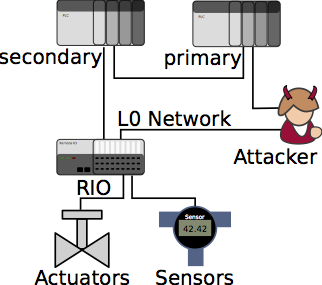
Risk Assessment for Cyber-Physical Systems
To evaluate the security and identify potential new threat vectors and vulnerabilities in cyber-physical systems, we need to consider attackers with detailed knowledge of the physical process, and we need to evaluate the potential negative impact they can cause in order to create reliable risk assessment profiles for the system.
Not Everything is Dark and Gloomy: Power Grid Protections Against IoT Demand Attacks USENIX Security 2019.
CPS: Driving Cyber-Physical Systems to Unsafe Operating Conditions by Timing DoS Attacks on Sensor Signals 30th Annual Computer Security Applications Conference (ACSAC) 2014.
A Framework for Evaluating Intrusion Detection Architectures in Advanced Metering Infrastructures. IEEE Transactions on Smart Grid 5(2) 2014.
Rethinking Security Properties, Threat Models, and the Design Space in Sensor Networks: A Case Study in SCADA Systems. Ad Hoc Networks, 7(8) 2009.
Understanding the Physical and Economic Consequences of Attacks on Control Systems. International Journal of Critical Infrastructure Protection 2(3) 2009.
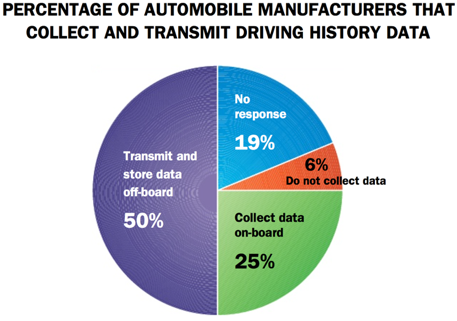
Security and Privacy in IoT
The ability of IoT to passively sense surrounding activity makes the privacy issues they raise distinct from the privacy issues raised by traditional computing systems. As they collect physical data of diverse human activities such as electricity consumption, location information, driving habits, and biosensor data at unprecedented levels of granularity, their passive manner of collection leaves people generally unaware of how much information about them is being gathered. We are studying new privacy enhancing technologies to allow CPS and IoT systems to fulfill their operational goals, while minimizing privacy risks to users of these technologies. We are also studying the advantages and disadvantages of differential privacy in control systems. We are also studying the implications of attacks on IoT devices and the consequences in the context of our socio-technical experiences.
Adversarial Classification under Differential Privacy NDSS 2020.
Stealing, Spying, and Abusing: consequences of Attacks on Interent of Things Devices IEEE Security and Privacy Magazine, 2019.
Improving the Security of Visual Challenges ACM Transactions on Cyber-Physical Systems, 2019.
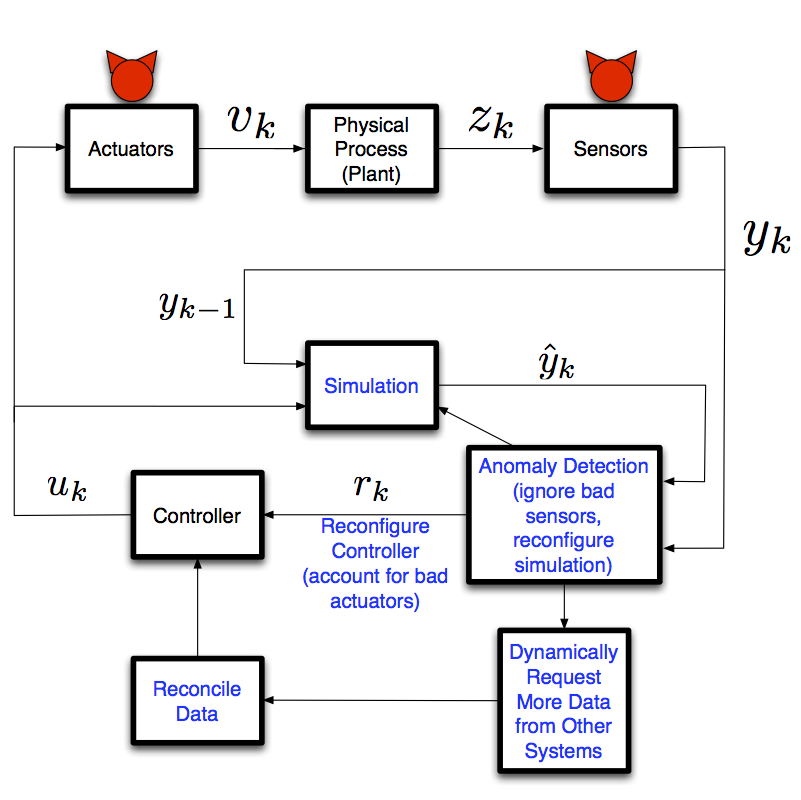
Attack-Resilient Cyber-Physical Systems
Resilient Cyber-Physical Systems need to operate safely and reliably, even when they have been partially compromised and are under active attacks. One way we have approached this problem, is to design a system conservatively so that it is able to withstand attacks (at the cost of increased operational costs). Another approach is to dynamically reconfigure the system when an attack is detected.
Safe and Secure Networked Control Systems Under Denial-Of-Service Attacks Hybrid Systems, Computation and Control (HSCC) 2009.
Controllability of Dynamical Systems: Threat Models and Reactive Security International Conference on Decision and Game Theory for Security (GameSec) 2013.
Integrity Attacks on Real-Time Pricing in Smart Grids: Impact and Countermeasures IEEE Transactions on Smart Grid 2016.
Incentives and Game Theory to Improve CPS Security
The protection of cyber-physical critical infrastructures against computer attacks is a matter of national security, public safety, and economic stability; however, most of our critical assets are owned and operated by private companies with pressing operational requirements, tight security budgets, and aversion to regulatory oversight. For most of these companies, creating a business case for improving computer security and for supporting long-term security research is a difficult task, partly because cybersecurity risk is almost impossible to measure, and partly because most companies managing critical infrastructures have not (yet) been subject to a major computer-based disruption. This has left our critical infrastructures fairly vulnerable to computer attacks and with technology that is decades behind the current security best practices used in other information technology domains. This line of research studies how to improve security investments by focusing on the design of incentives for investing in protecting our critical infrastructures.
Perverse Incentives in Security Contracts: A Case Study in the Colombian Power Grid Workshop on the Economics of Information Security (WEIS) 2016.
CPS: Market Analysis of Attacks Against Demand Response in the Smart grid 30th Annual Computer Security Applications Conference (ACSAC) 2014.
Game Theoretic Models of Electricity Theft Detection in Smart Utility Networks IEEE Control Systems V 35 Issue 1. 2015.
Work Outside of CPS Security
Network Security, Machine Learning, IoT, and Wireless Networks
Our lab is interested in network security monitoring and intrusion detection, and more recently, in the security of Software Defined Networks (SDN) and Network Function Virtualization (NFV). We also work on Machine Learning, big data analytics, and alert correlation in ways that improve ROC curves. Finally, we also work on wireless networking with lossy and unreliable links, which are frequent in embedded systems and IoT devices. We have been working on flexible data forwarding mechanisms (within the IETF) that can work within 6LoWPAN, or on IPv6 networks. We have also worked on MAC-layer anomaly detection, which can help identify networking cards that have not implemented correctly the backoff mechanisms to prevent nodes from getting unfair share of the spectrum.
A Framework for the Evaluation of Intrusion Detection Systems. IEEE Symposium on Security and Privacy, 2006.
Big Data Analytics for Security IEEE security & privacy, 11(6) 2013.
Optimal ROC Curve for a Combination of Classifiers Advances in Neural Information Processing Systems (NIPS) 2008.
Semantic middleware for the Internet of Things Internet of Things (IOT) 2010.
Depth-First Forwarding (DFF) in Unreliable Networks. IETF Experimental Standard. RFC6971. 2013
Performance Comparison of Detection Schemes for MAC Layer Misbehavior IEEE INFOCOM 2007.